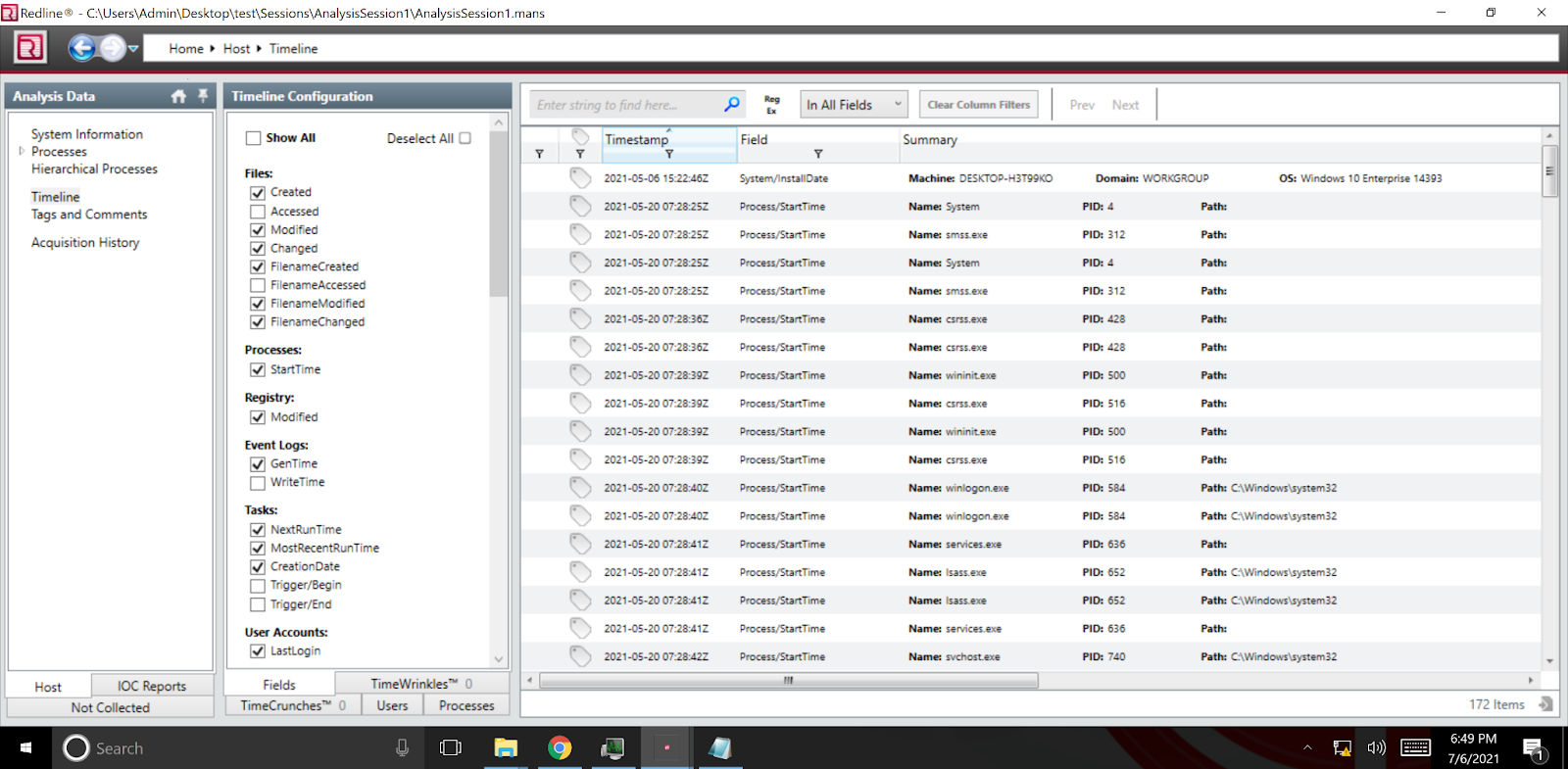
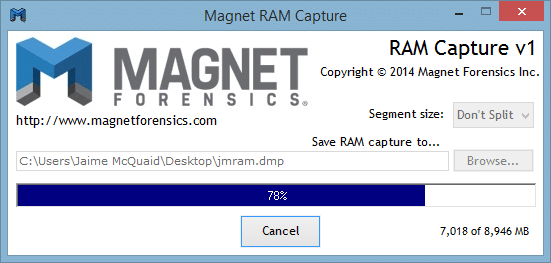
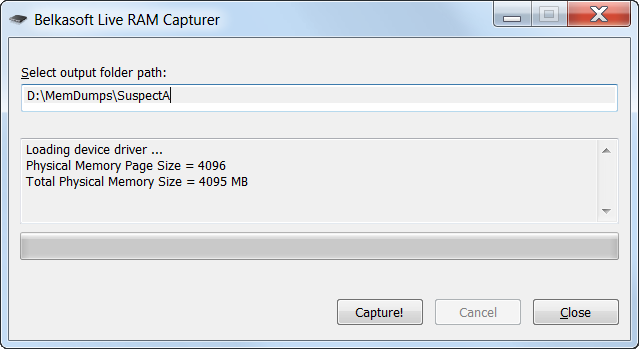
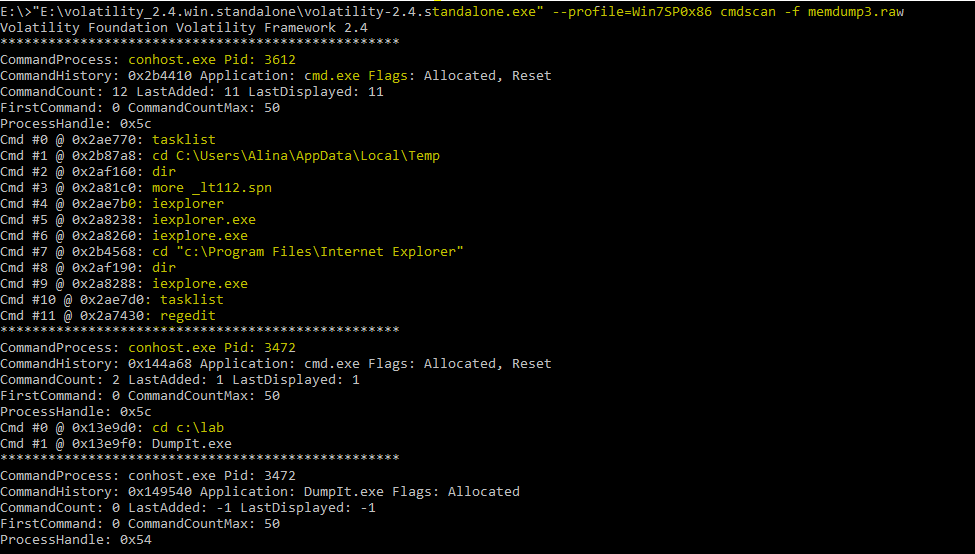
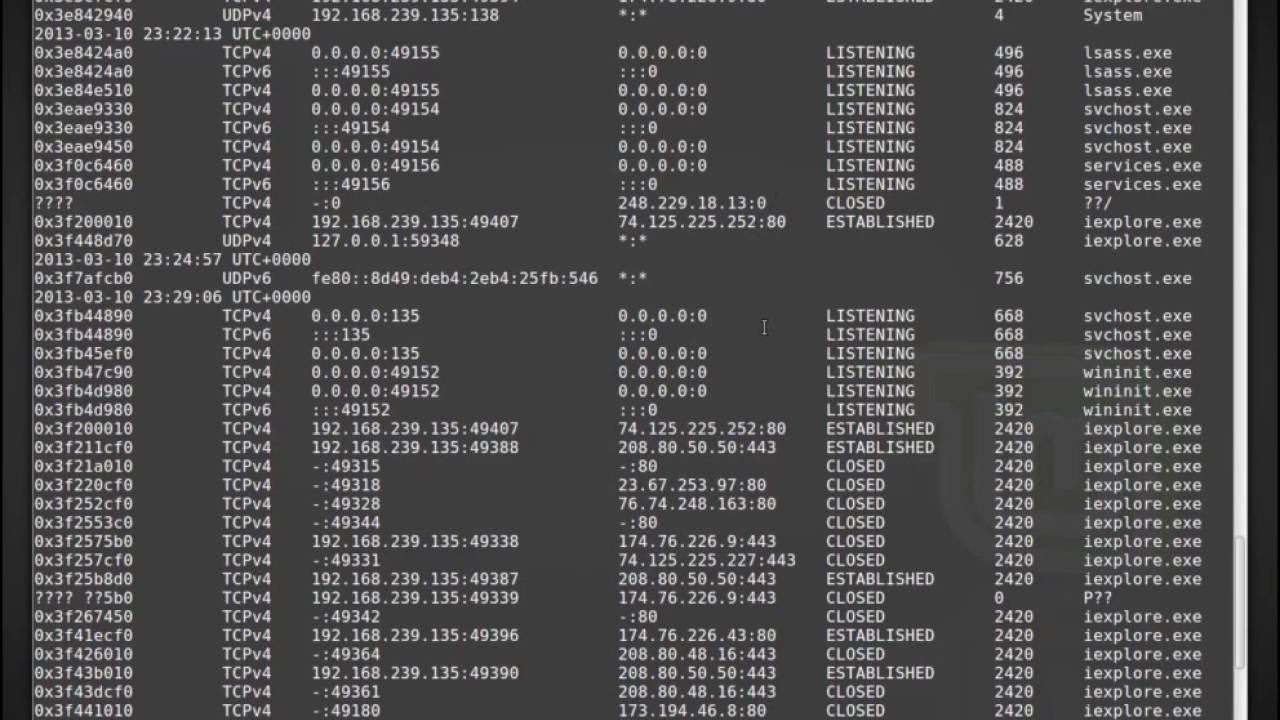
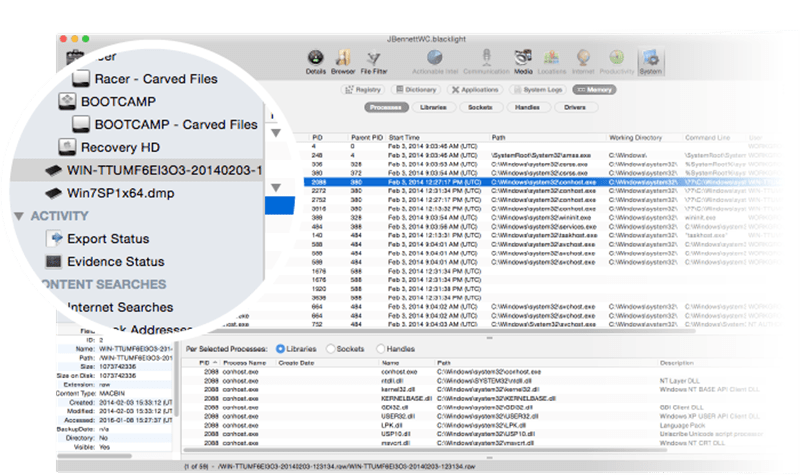
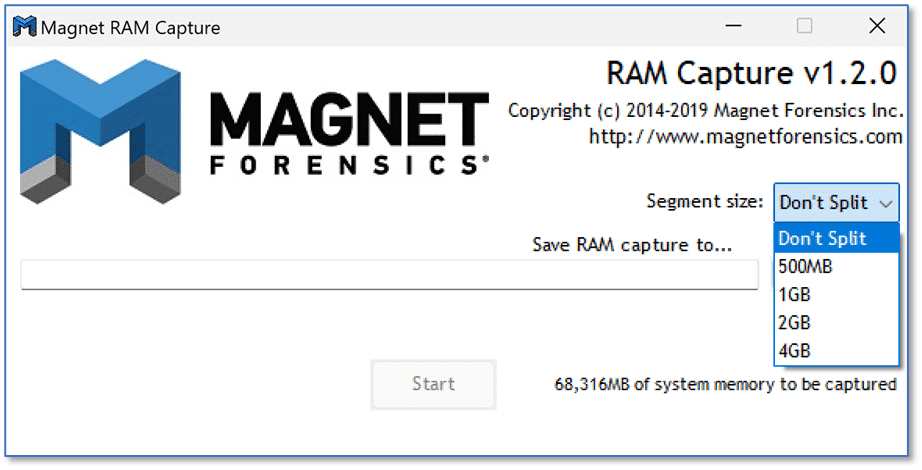
Memory forensics tools: Comparing processing time and left artifacts on volatile memory | Semantic Scholar
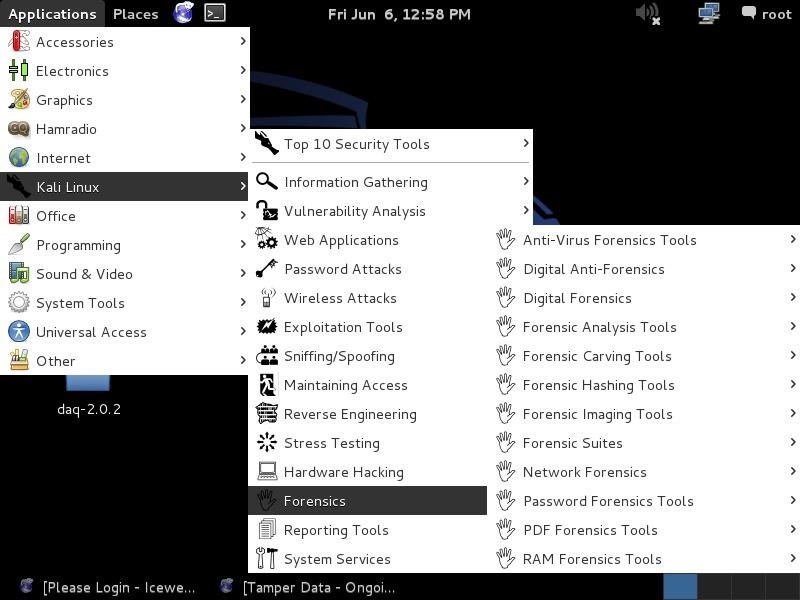
Hack Like a Pro: Digital Forensics Using Kali, Part 1 (The Tools of a Forensic Investigator) « Null Byte :: WonderHowTo

Kenya CyberSecurity & Forensics Association: KCSFA on Twitter: "Why do you need to consider live memory forensics when a cyber attack is actively taking place Incase its a mission critical system To